nullifier
Deriving a nullifier within an app contract
Let's assume a developer wants a nullifier of a note to be derived as:
nullifier = h(note_hash, nullifier_key);
... where the nullifier_key () belongs to the 'owner' of the note, and where the 'owner' is some .
Here's example for how an app circuit could constrain the nullifier key to be correct:
Diagram
It's easiest to take a look at this first:
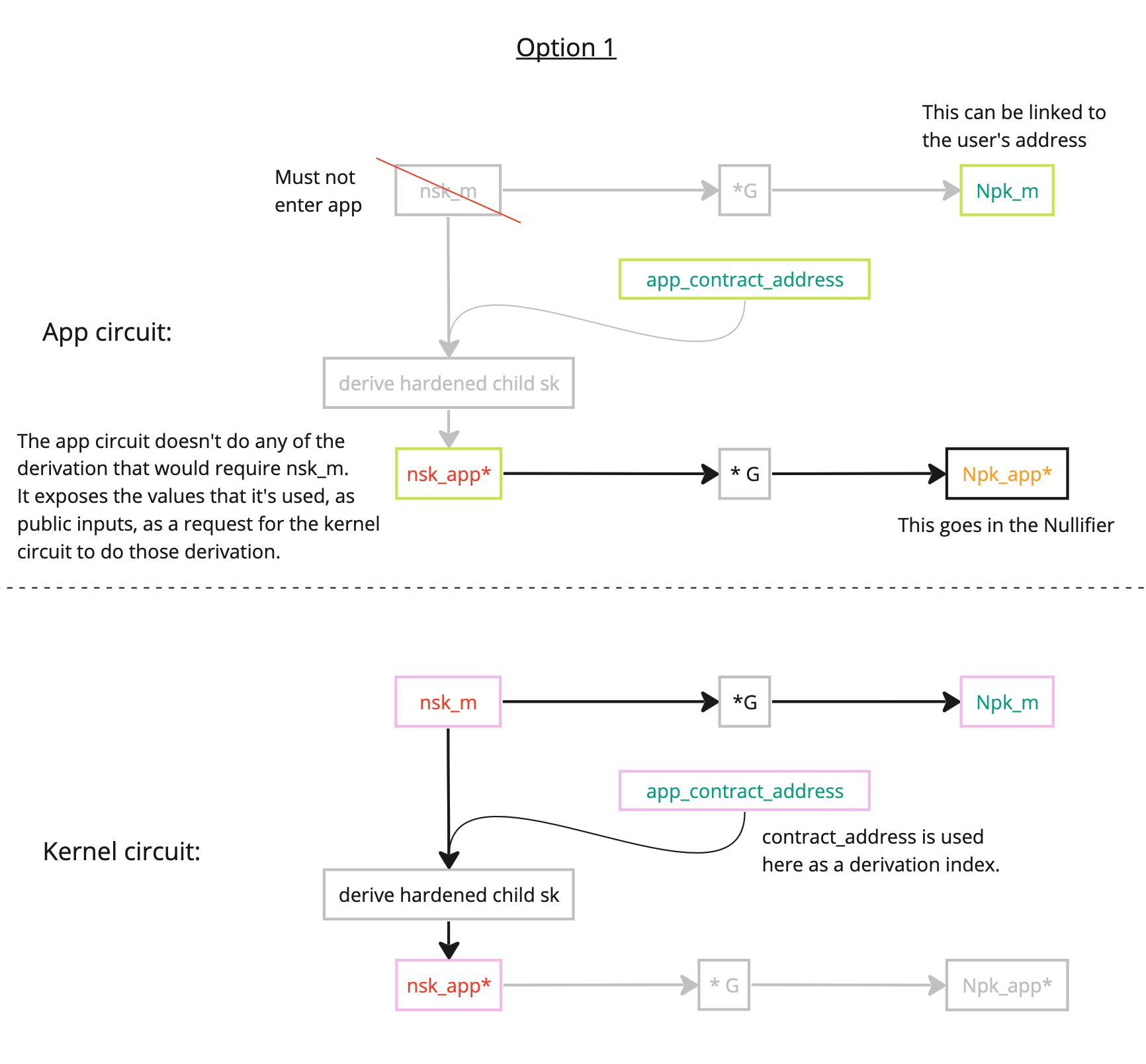
Within the app circuit
Within the app, we can prove links between:
The link that's missing is to prove that relates to . To compute this missing link requires the , which MUST NOT be passed into an app circuit, and may only be passed into a kernel circuit. See the next 'Within the kernel circuit' section for details of this logic.
The logic
Note: the passing of points directly into the poseidon function is lazy notation: the keys would need to be serialized appropriately as fields into the poseidon function.
Recall an important point: the app circuit MUST NOT be given . Indeed, is derived (see earlier) as a hardened child of , to prevent from being reverse-derived by a malicious circuit. The linking of to is deferred to the kernel circuit (which can be trusted moreso than an app).
Recall also: is used (instead of ) solely as a way of giving the user the option of sharing with a trusted 3rd party, to give them the ability to view when a note has been nullified (although I'm not sure how useful this is, given that it would require brute-force effort from that party to determine which note hash has been nullified, with very little additional information).
The app circuit exposes, as public inputs, a "nullifier key validation request":
let nullifier_validation_request = KeyValidationRequest {
app_address: app_address,
claimed_hardened_child_sk: nsk_app,
claimed_parent_pk: Npk_m,
}
Within the Kernel Circuit
The kernel circuit can then validate the request (having been given as a private input to the kernel circuit):
If the kernel circuit succeeds in these calculations, then the has been validated as having a known secret key, and belonging to the .